http://www.earthvpn.com/how-to-configure-openvpn-on-ubuntu-linux/
利用jekyll在github上搭建博客
准备搭建环境
由于博主使用的Ubuntu 14.10, 以下命令主要适用于Ubuntu, 其他Linux系统以及Mac系统请视情况而定
- github 账号
- git
- ruby
- python
创建你的git repo
在github上创建同名的repo USERNAME.github.com
克隆一份jekyll的代码到本地, 并推送到你的repo上
git clone https://github.com/plusjade/jekyll-bootstrap.git USERNAME.github.com cd USERNAME.github.com git remote set-url origin git@github.com:USERNAME/USERNAME.github.com.git git push origin master
过几分钟,就可以看到 http://USERNAME.github.io 已经更新了
在本机安装jekyll server
ruby1.9.1-dev中包含gem的安装包
sudo apt-get install ruby1.9.1-dev
安装jekyll
sudo gem1.9.1 install jekyll
test jekyll
jekyll serve
如果你启动jekyll时遇到Could not find a JavaScript runtime. See https://github.com/sstephenson/exec 请JavaScript引擎,如nodejs sudo apt-get install nodejs
rake
sudo gem1.9.1 install rake
theme
rake theme:install git="https://github.com/jekyllbootstrap/theme-twitter.git"
配置jekyll
修改_config.yml文件
将一些基础信息配置成想要的内容
添加文章
在_posts目录下新建一个markdown(*.md)文件, 文件命名规范是yyyy-mm-dd-url, 例如该文章的文件为2012-01-01-test.md
得到的访问路径却是 /javascript/2012/01/01/test/
其中/javascript是在markdown文件中配置的.
markdown文件头需要几个配置, 以下是该文章的头配置
--- layout: post title: 在github上搭建博客 category: javascript tags: [github, bootstrap, jekyll, javascript] ---
每个markdown必须在头部加上这段. 然后下面直接写markdown代码就行了.
配置域名
新建一个
CNAME文件, 里面直接写上所配置的域名, 例如sundp.me
然后上域名提供商上配置域名解析, A记录到207.97.227.245
等待域名解析完毕即可, 直接访问http://sundapeng.github.io 会跳转至 http://sundp.me
duoshuo
vim _config.yml
comments :
provider : duoshuo
duoshuo :
short_name : sdp-githubvim ./_includes/JB/comments
{% when "facebook" %}
{% include JB/comments-providers/facebook %}
{% when "duoshuo" %}
{% include JB/comments-providers/duoshuo %}
{% when "custom" %}
{% include custom/comments %}vim _includes/JB/comments-providers/duoshuo
<!-- Duoshuo Comment BEGIN -->
<!-- 多说评论框 start -->
<div id="comments">
<div class="ds-thread" {% if page.id %}data-thread-key="{{ page.id }}"{% endif %} data-title="{% if page.title %}{{ page.title }} - {% endif %} " {{ site.title }}"></div>
</div>
<!-- 多说评论框 end -->
<!-- 多说公共JS代码 start (一个网页只需插入一次) -->
<script type="text/javascript">
var duoshuoQuery = {short_name:"sdp-github"};
(function() {
var ds = document.createElement('script');
ds.type = 'text/javascript';ds.async = true;
ds.src = (document.location.protocol == 'https:' ? 'https:' : 'http:') + '//static.duoshuo.com/embed.js';
ds.charset = 'UTF-8';
(document.getElementsByTagName('head')[0] || document.getElementsByTagName('body')[0]).appendChild(ds);
})();
</script>
<!-- 多说公共JS代码 end -->
<!-- Duoshuo Comment END -->baidu
vim _config.yml
analytics :
provider : baidu
baidu :
key : '112e9d845f2671e7bbe63d9c143ead10'
google :
tracking_id : 'UA-123-12'vim _includes/JB/analytics
{% when "baidu" %}
{% include JB/analytics-providers/baidu %}{% when "piwik" %}
{% include JB/analytics-providers/piwik %}
{% when "baidu" %}
{% include JB/analytics-providers/baidu %}
{% when "custom" %}
{% include custom/analytics %}
{% endcase %}vim _includes/JB/analytics-providers/baidu
<script>
var _hmt = _hmt || [];
(function() {
var hm = document.createElement("script");
hm.src = "//hm.baidu.com/hm.js?{{ site.JB.analytics.baidu.key }}";
var s = document.getElementsByTagName("script")[0];
s.parentNode.insertBefore(hm, s);
})();
</script>highlight
sudo apt-get install python-pip
pip install pygments --user
sudo gem1.9.1 install pygments.rb
sudo apt-get install python-pygmentspygmentize -S default -f html > assets/themes/bootstrap-3/css/pygments-friendly.css
vim ./_includes/themes/bootstrap-3/default.html 加入
<link href="/assets/themes//css/pygments.css" rel="stylesheet" type="text/css">OpenVPN over HTTP ,突破宽带服务商的网速限制
Why
我家里用的是一家三线的便宜小区宽带,标称有几个M的带宽,虽说有些资源确实能达到这个速度,但发现直连VPN的速度从来都没上去过,大概30k/s,不难猜测到,ISP在链路上做了手脚,即所谓的Layer 7 Priority QoS。因为入线是100M进宅然后PPPoE,不像ADSL那样直接物理链路就限制了连接速度,在链路层做QoS也很合理。平时HTTP打开网页、下载到合适链路的话很容易达到满速,而OpenVPN的TCP/UDP包估计就被当成P2P流量被限制了,所以网速一点都不给力。
用OpenVPN科学上网是最稳定最灵活的方式了,它基于udp/tcp的协议,比pptp、l2tp等直接跑IP包的开销虽说大一点,但好处就是容易把数据流重新封装,避开链路的关卡。显然它也支持HTTP代理,所以把OpenVPN变成HTTP协议,就可以在家里跑上满速的VPN。
How
OpenVPN要过HTTP代理,只能用TCP协议,这个需要服务端和客户端都要稍作修改。
Polipo as Tunnel Proxy
首先在VPS上安装一个http proxy,我选择polipo,比较轻量级。
apt-get install polipo
|
配置也是很简单的,编辑/etc/polipo/config,原来的配置文件基本全都是注释,直接在文件底部加上:
proxyAddress = "0.0.0.0" proxyPort = 8128 authCredentials = "user:password3.141592654" tunnelAllowedPorts = 1194 |
- polipo默认只监听本地的127.0.0.1,要拿来做服务就要监听外网
- polipo默认监听8123,为了不让扫代理的盯上,自己随便写个端口
- 加上http basic验证,这个密码不要紧,后面让openvpn自动应答
- 允许管道模式连接openvpn的1194端口
OpenVPN
Server
服务端倒是不需要很多配置,确定是tcp模式监听连接(我是多开一个openvpn server,子网错开,个人喜欢吧)
Client
客户端就要指定使用代理的方式:
remote 127.0.0.1 1194 http-proxy YOUR.VPS.IP.HERE.com 8128 pw.txt http-proxy-retry |
这个pw.txt是上述的HTTP的认证信息,用户名密码各一行。
现在连接OpenVPN,可以看到连接过程的Log有这么几句,基本就确定OpenVPN over HTTP成功了!
Sun Mar 4 19:12:58 2012 Attempting to establish TCP connection with 199.101.103.107:8192 [nonblock] Sun Mar 4 19:12:59 2012 TCP connection established with [IPADDR]:8128 Sun Mar 4 19:12:59 2012 Send to HTTP proxy: 'CONNECT 127.0.0.1:1194 HTTP/1.0' Sun Mar 4 19:12:59 2012 Attempting Basic Proxy-Authorization Sun Mar 4 19:13:00 2012 HTTP proxy returned: 'HTTP/1.1 200 Tunnel established' |
Related
最后透露一下我的科学上网环境是在跑OpenWRT的路由器上跑VPN,然后配合chnroute的路由表,当然dnsmasq也经过配置负责把国内常用域名的解释交给国内的114.114.114.114服务器,这样基本一回家手机kindle电脑等全都是翻墙环境,而且速度非常良好。
Reference
-------------------------------
OpenVPN config files generator
It’s not extremly difficult to set up an openvpn server, but you have to deal with certificates, rsa keys, configs, subnet addresses, iptables … such trifles are annoying.
So I wrote this script to make my life easier, only to provide essential infomation like the server IP, and configuraion will be done at the background, then tared packages are ready for both servers and clients.
Source is available at Github. Pull requests are welcome.
The script is recommanded running at your work station, and then upload only the server part to the server, for secure considerations.
Features
- Provide tared config which ready for any server distribution.
- Random VPN subnet will be generated to avoid conflict.
- Random digital subffixed server/client CommonName will be assigned (if you don’t provide one) for clearer management.
- All those config files are based on examples that ship together within your distribution.
- tls-auth enabled by default.
Usage
For new setup:
./much-easier-rsa-menu.sh
|
Just do as promoted. When select 5 to exit, all the files will be packed into a single NAME-all.tar.gz, you should save it to somewhere safe. And if you want to sign some more certificate from this root ca, put this tar file as the argument.
./much-easier-rsa-menu.sh /path/to/YOUR-VPN-all.tar.gz |
At last the script also provide you iptables commands that can be useful to setup the server as a VPN gateway.
Download
Direct download via wget/curl should be ok:
https://github.com/pentie/much-easier-rsa-for-openvpn/raw/master/much-easier-rsa-menu.sh
项目地址:
你也来做个SS服务商吧】【附域名解析和加速】SS网站一键搭建-感谢91vps.club的强力支持
执行:
screen -S ss
wget -N --no-check-certificate https://raw.githubusercontent.com/mmmwhy/ss-panel-and-ss-py-mu/master/ss-panel_node.sh && chmod +x ss-panel_node.sh && bash ss-panel_node.sh
7.登陆后台修改管理员账号和密码(修改后请务必牢记)。
8.进入ss-panel页面后,记得在管理面板->节点管理->添加节点->输入节点信息。
三、重启服务器后无法登陆网站的解决方案
如果在重启服务器后无法登陆网站,需要在Xshell等软件中执行
supervisord
即可。
四、安装加速程序
【BBR程序】
1.在 Xshell 执行:
wget --no-check-certificate https://github.com/teddysun/across/raw/master/bbr.sh
再执行:
chmod +x bbr.sh
再执行:
./bbr.sh
2.安装完成后,脚本会提示需要重启 VPS,输入 y 并回车后重启。
重启完成后,验证一下是否成功安装最新内核并开启 TCP BBR,
输入以下命令:
uname -r
查看内核版本,含有 4.11 就表示 OK。
执行下面命令:
lsmod | grep bbr
返回值有 tcp_bbr 模块即说明bbr已启动。
五、添加另一个节点
你会觉得一个节点似乎不够使用,比如你现在是洛杉矶节点,需要再添加一个东京节点。方法如下:
1.登陆你的IP地址,进入管理员面板,在管理面板->节点管理->添加节点->输入节点信息。记住该节点的ID。
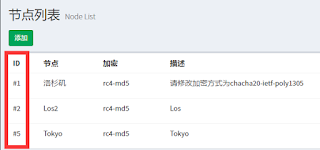 |
| 红框内的就是,忽视#号 |
有时候你会觉得使用IP地址登陆网站有点low,这个时候你可以为自己买一个域名,然后将域名解析到你的服务器公网IP上。
这里使用的是万网注册域名,你需要需要万网账号(用天猫账号就可以登陆),然后购买一个你中意的域名,付款买下(千万不要买.cn的域名!)。
在你的阿里云控制台内-域名下。选择解析,输入你的服务器公网IP,稍等片刻即可解析成功。
现在在浏览器中输入你的域名,是不是已经可以访问了?(不能访问的,需要更改本地网络的DNS 8.8.8.8)
当然你也可以来我的SS站点玩耍withings.space
本教程代码使用了李飞阳的教程,飞阳的网站中有大量的技术博文,欢迎大家关注!
任何疑问,Telegram.
Centos6下,编译ocserv
1
Centos7使用epel源可直接使用Yum安装。
安装编译环境及依赖,如部分软件不能安装请先安装epel源。
yum install pam-devel readline-devel http-parser-devel unbound gmp-devel
yum install tar gzip xz wget gcc make autoconf
ocserv编译安装依赖,ocserv需要gnutls3版本以上,gnutls依赖nettle2.7.1:
wget ftp://ftp.gnu.org/gnu/nettle/nettle-2.7.1.tar.gz
tar zxvf nettle-2.7.1.tar.gz
cd nettle-2.7.1/
./configure --prefix=/usr/local/nettle
make && make install
echo '/usr/local/nettle/lib64/' > /etc/ld.so.conf.d/nettle.conf
ldconfig
安装gnutls3.3.9:
export NETTLE_CFLAGS="-I/usr/local/nettle/include/"
export NETTLE_LIBS="-L/usr/local/nettle/lib64/ -lnettle"
export HOGWEED_LIBS="-L/usr/local/nettle/lib64/ -lhogweed"
export HOGWEED_CFLAGS="-I/usr/local/nettle/include"
wget ftp://ftp.gnutls.org/gcrypt/gnutls/v3.3/gnutls-3.3.9.tar.xz
tar xvf gnutls-3.3.9.tar.xz
cd gnutls-3.3.9/
./configure --prefix=/usr/local/gnutls
make && make install
ln -s /usr/local/gnutls/bin/certtool /usr/bin/certtool
echo '/usr/local/gnutls/lib/' > /etc/ld.so.conf.d/gnutls.conf
ldconfig
安装libnl:
yum install bison flex
wget http://www.carisma.slowglass.com/~tgr/libnl/files/libnl-3.2.24.tar.gz
tar xvf libnl-3.2.24.tar.gz
cd libnl-3.2.24
./configure --prefix=/usr/local/libnl
make && make install
echo '/usr/local/libnl/lib/' > /etc/ld.so.conf.d/libnl.conf
ldconfig
安装ocserv:
export LIBNL3_CFLAGS="-I/usr/local/libnl/include/libnl3"
export LIBNL3_LIBS="-L//usr/local/libnl/lib/ -lnl-3 -lnl-route-3"
export LIBGNUTLS_LIBS="-L/usr/local/gnutls/lib/ -lgnutls"
export LIBGNUTLS_CFLAGS="-I/usr/local/gnutls/include/"
wget ftp://ftp.infradead.org/pub/ocserv/ocserv-0.9.0.1.tar.xz
tar xvf ocserv-0.9.0.1.tar.xz
cd ocserv-0.9.0
./configure --prefix=/usr/local/ocserv
make && make install
echo 'export PATH=$PATH://usr/local/ocserv/sbin/:/usr/local/ocserv/bin/' >> $HOME/.bashrc
source $HOME/.bashrc
生成SSL证书:
mkdir /etc/ocserv/
cd /etc/ocserv
#CA私钥:
certtool --generate-privkey --outfile ca-key.pem
#CA模板:
cat ca.tmpl
cn = "www.haiyun.me"
organization = "www.haiyun.me"
serial = 1
expiration_days = 3650
ca
signing_key
cert_signing_key
crl_signing_key
#CA证书:
certtool --generate-self-signed --load-privkey ca-key.pem --template ca.tmpl --outfile ca-cert.pem
#Server私钥:
certtool --generate-privkey --outfile server-key.pem
#Server证书模板:
cat server.tmpl
cn = "www.haiyun.me"
o = "www.haiyun.me"
expiration_days = 3650
signing_key
encryption_key
tls_www_server
#Server证书:
certtool --generate-certificate --load-privkey server-key.pem --load-ca-certificate ca-cert.pem --load-ca-privkey ca-key.pem --template server.tmpl --outfile server-cert.pem
密码登录,生成密码文件:
ocpasswd -c /etc/ocserv/ocpasswd username
证书登录:
#user私钥
certtool --generate-privkey --outfile user-key.pem
#user模板
cat user.tmpl
cn = "some random name"
unit = "some random unit"
expiration_days = 365
signing_key
tls_www_client
#user证书
certtool --generate-certificate --load-privkey user-key.pem --load-ca-certificate ca-cert.pem --load-ca-privkey ca-key.pem --template user.tmpl --outfile user-cert.pem
配置文件:
auth = "plain[/etc/ocserv/ocpasswd]"
#证书认证
#auth = "certificate"
ca-cert /etc/ocserv/ca-cert.pem
max-clients = 16
max-same-clients = 2
tcp-port = 5551
udp-port = 5551
keepalive = 32400
try-mtu-discovery = true
cisco-client-compat = true
server-cert = /etc/ocserv/server-cert.pem
server-key = /etc/ocserv/server-key.pem
auth-timeout = 40
pid-file = /var/run/ocserv.pid
socket-file = /var/run/ocserv-socket
run-as-user = nobody
run-as-group = daemon
device = vpns
ipv4-network = 192.168.1.0
ipv4-netmask = 255.255.255.0
route = 192.168.1.0/255.255.255.0
启动opserv:
ocserv -c /etc/ocserv/ocserv.conf
IP转发及SNAT:
echo 1 > /proc/sys/net/ipv4/ip_forward
echo "echo 1 > /proc/sys/net/ipv4/ip_forward " >> /etc/rc.local
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
使用用户密码连接:
echo passwd|openconnect -u username www.haiyun.me:5551 --no-cert-check
使用证书连接:
openconnect -k user-key.pem -c user-cert.pem www.haiyun.me:5551 --no-cert-check
from http://www.haiyun.me/archives/1071.html
---------------------
Anyconnect 服务器的搭建以及与 Radius 验证的整合
根据上面的教程衍生和记录而来。
Centos 6 x64 下进行。
1、依赖:
yum install pam-devel readline-devel http-parser-devel unbound gmp-devel
yum install tar gzip xz wget gcc make autoconf
2、安装 nettle:
cd
wget https://ftp.gnu.org/gnu/nettle/nettle-3.1.tar.gz
tar zxvf nettle-3.1.tar.gz
cd nettle-3.1/
./configure --prefix=/usr/local/nettle
make && make install
echo '/usr/local/nettle/lib64/' > /etc/ld.so.conf.d/nettle.conf
ldconfig
3、安装gnutls:
cd
export NETTLE_CFLAGS="-I/usr/local/nettle/include/"
export NETTLE_LIBS="-L/usr/local/nettle/lib64/ -lnettle"
export HOGWEED_LIBS="-L/usr/local/nettle/lib64/ -lhogweed"
export HOGWEED_CFLAGS="-I/usr/local/nettle/include"
wget ftp://ftp.gnutls.org/gcrypt/gnutls/v3.4/gnutls-3.4.7.tar.xz
tar xvf gnutls-3.4.7.tar.xz
cd gnutls-3.4.7
./configure --prefix=/usr/local/gnutls --with-included-libtasn1 --without-p11-kit
make && make install
ln -s /usr/local/gnutls/bin/certtool /usr/bin/certtool
echo '/usr/local/gnutls/lib/' > /etc/ld.so.conf.d/gnutls.conf
ldconfig
4、安装 libnl:
cd
yum install bison flex
wget https://www.infradead.org/~tgr/libnl/files/libnl-3.2.25.tar.gz
tar xvf libnl-3.2.25.tar.gz
cd libnl-3.2.25
./configure --prefix=/usr/local/libnl
make && make install
echo '/usr/local/libnl/lib/' > /etc/ld.so.conf.d/libnl.conf
ldconfig
5、安装radius相关:
export LIBNL3_CFLAGS="-I/usr/local/libnl/include/libnl3"
export LIBNL3_LIBS="-L//usr/local/libnl/lib/ -lnl-3 -lnl-route-3"
export LIBGNUTLS_LIBS="-L/usr/local/gnutls/lib/ -lgnutls"
export LIBGNUTLS_CFLAGS="-I/usr/local/gnutls/include/"
wget https://github.com/radcli/radcli/releases/download/1.2.5/radcli-1.2.5.tar.gz
tar xvzf radcli-1.2.5.tar.gz
cd radcli-1.2.5
./configure --prefix=/usr/local/radcli
echo '/usr/local/radcli/lib/' > /etc/ld.so.conf.d/radcli.conf
make && make install
ldconfig
yum install freeradius-client -y
6、安装ocserv:
export RADCLI_LIBS="-L/usr/local/radcli/lib/ -lradcli"
export RADCLI_CFLAGS="-I/usr/local/radcli/include/"
wget ftp://ftp.infradead.org/pub/ocserv/ocserv-0.10.9.tar.xz
tar xvf ocserv-0.10.9.tar.xz
cd ocserv-0.10.9
编辑src/vpn.h:
#define DEFAULT_CONFIG_ENTRIES 96
改成 200
./configure --prefix=/usr/local/ocserv
make && make install
echo 'export PATH=$PATH://usr/local/ocserv/sbin/:/usr/local/ocserv/bin/' >> $HOME/.bashrc
source $HOME/.bashrc
7、证书相关
这里因为我有个泛域名证书,所以就不生成了= =直接用。
mkdir /etc/ocserv/
编辑 /etc/ocserv/server-cert.pem ,把证书文件贴进去,记住只贴一个,就是颁发给你的证书= =你贴证书链后面会报错= =貌似是 CA 证书不科学的原因。
然后:
chmod 600 /etc/ocserv/server-cert.pem
还有 server-key.pem ,也是一样的,密钥粘进去,权限设置好。
8、freeradius-client 的设置
我这里只做了登陆的验证。
编辑/etc/radiusclient/radiusclient.conf:
yourserveraddress 指代 radius 服务器地址。
authserver yourserveraddress:1812
acctserver yourserveraddress:1813
dictionary /etc/radiusclient/dictionary
同时记住 radius 服务器要添加好权限。
然后是编辑 /etc/radiusclient/servers ,
添加
yourserveraddress 指代 radius 服务器地址。yourserversecret 指代 radius 服务器密钥。
youserveraddress yourserversecret
9、配置文件
配置文件的话,我们回到刚才编译 ocserv 的目录。
cd /root/ocserv-0.10.9
cp ./tests/docker-ocserv/ocserv-radius.conf /etc/ocserv/ocserv.conf
然后编辑 /etc/ocserv/ocserv.conf
主要修改以下几个:
try-mtu-discovery = true
cisco-client-compat = true
server-cert = /etc/ocserv/server-cert.pem
server-key = /etc/ocserv/server-key.pem
max-clients = 50
max-same-clients = 10
tcp-port = 5444
udp-port = 5444
dns = 8.8.8.8
dns = 8.8.4.4
ipv4-network = 192.168.10.0
occtl-socket-file = /var/run/occtl.socket
#ca-cert=。。。。 对没错注释掉。
还有特别注意路由表,先把 no-route 和 route 都给注释了,然后添加以下配置。
route = 103.0.0.0/255.0.0.0
route = 106.0.0.0/255.0.0.0
route = 107.0.0.0/255.0.0.0
route = 108.0.0.0/255.0.0.0
route = 141.0.0.0/255.0.0.0
route = 153.0.0.0/255.0.0.0
route = 160.0.0.0/255.0.0.0
route = 166.0.0.0/255.0.0.0
route = 17.0.0.0/255.0.0.0
route = 173.0.0.0/255.0.0.0
route = 176.0.0.0/255.0.0.0
route = 178.0.0.0/255.0.0.0
route = 184.0.0.0/255.0.0.0
route = 194.0.0.0/255.0.0.0
route = 198.0.0.0/255.0.0.0
route = 199.0.0.0/255.0.0.0
route = 203.0.0.0/255.0.0.0
route = 204.0.0.0/255.0.0.0
route = 205.0.0.0/255.0.0.0
route = 208.0.0.0/255.0.0.0
route = 209.0.0.0/255.0.0.0
route = 210.0.0.0/255.0.0.0
route = 216.0.0.0/255.0.0.0
route = 3.0.0.0/255.0.0.0
route = 4.0.0.0/255.0.0.0
route = 31.0.0.0/255.0.0.0
route = 46.0.0.0/255.0.0.0
route = 50.0.0.0/255.0.0.0
route = 54.0.0.0/255.0.0.0
route = 61.0.0.0/255.0.0.0
route = 64.0.0.0/255.0.0.0
route = 67.0.0.0/255.0.0.0
route = 68.0.0.0/255.0.0.0
route = 69.0.0.0/255.0.0.0
route = 70.0.0.0/255.0.0.0
route = 72.0.0.0/255.0.0.0
route = 74.0.0.0/255.0.0.0
route = 75.0.0.0/255.0.0.0
route = 76.0.0.0/255.0.0.0
route = 77.0.0.0/255.0.0.0
route = 79.0.0.0/255.0.0.0
route = 8.0.0.0/255.0.0.0
route = 23.0.0.0/255.0.0.0
route = 93.0.0.0/255.0.0.0
route = 96.0.0.0/255.0.0.0
route = 100.0.0.0/248.0.0.0
route = 109.0.0.0/255.0.0.0
route = 128.0.0.0/255.0.0.0
route = 174.0.0.0/255.0.0.0
route = 190.0.0.0/255.0.0.0
route = 192.0.0.0/255.0.0.0
OK,保存。
9、防火墙&系统配置
echo 1 > /proc/sys/net/ipv4/ip_forward
echo "echo 1 > /proc/sys/net/ipv4/ip_forward " >> /etc/rc.local
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
service iptables save
10、运行 ocserv
ocserv -f -c /etc/ocserv/ocserv.conf
可以连接了。此处不再赘述。
把这行加进 /etc/rc.local 就可以开机自启动了。
使用通用Linux脚本,简化Linux Shell脚本的开发
在编写Shell脚本时,因发行版不同,要获取系统名称、版本、虚拟化技术、安装软件包等成为了一件非常麻烦的事情。现在,有了通用Linux脚本,一切都变得简单了。
何为通用Linux脚本?
通用Linux脚本(Universal Linux Script,ULS,发音:”U-Less”)是我开发的一种Linux脚本,有如下的特点:
语言上:与Shell脚本语法完全相同
功能上:内置了常用的系统信息变量库和常用命令变量库,只需几个字母就能轻松存取
使用上:提供ULS一键安装脚本来安装Python写的ULS翻译程序,执行脚本只需一个命令
OK,我们来看两个例子:
第一,Deb系的OS从源安装软件要用 “apt-get -y install“,RH系的OS用”yum -y install“。在ULS中,全部以 pkg.install 代替。ULS脚本在执行时会自动替换为对应不同OS的命令。
第二,是否需要在脚本中判断VPS的虚拟化技术、获取CPU信息、发行版名称及版本?在ULS中,可以使用 dev.virt 、dev.cpu、sys.name、sys.version 代替。在脚本执行时,上述变量会自动被替换为带有两个双引号的字符串,比如:
echo dev.virt
在执行时会根据系统信息被替换为:
echo "kvm"
看过了两个实例,是不是对ULS增进了一些了解呢?下面开始正式的题目了:
安装与使用
ULS代码托管在Github,基于GPLv3开放源代码。地址是:
https://github.com/CYRO4S/Universal-Linux-Script
目前ULS已经配备了完整的文档,包括安装和使用。非常简单,易于操作,没有技术性障碍。
简易安装
简易安装真的很简易,只需要一行命令,推荐使用:
wget https://raw.githubusercontent.com/CYRO4S/Universal-Linux-Script/master/uls_install.sh && bash uls_install.sh
这个一键安装脚本将安装 wget、python3 和 virt-what,下载uls.py,并运行一遍系统信息获取,之后会将获取的系统信息存储在 device.json 中,以供执行ULS脚本时替换。
执行ULS脚本
很简单,使用:
uls [ULS脚本路径]
就可以了。若ULS脚本以“#!/usr/bin/uls”开头,且有可执行权限,使用:
./[ULS脚本名]
就可以了。
重新运行系统信息获取
若您的硬件、软件、网路进行过更改,建议您重新运行系统信息获取。使用
uls --getinfo
来重新获取。ULS也将同时更新 device.json 中的内容。
升级ULS
新版的ULS会支持更多的功能。使用:
uls --update
来升级ULS到最新版本。
所有内置的变量和语句
参阅Wiki:
https://github.com/CYRO4S/Universal-Linux-Script/wiki/All-built-in-variables
树莓派2 Kali Linux 2.1 自动配置脚本
今天准备打造一个完美的HACKBOX,于是边进行配置边写了这个脚本。
或执行:
脚本说明
执行脚本时会让用户选择步骤,输入1到4的数字按下回车即可执行相应步骤。
步骤分别为:
- 禁用过扫描(去除黑边) — 配置中科大源 — 启用WiFi(会要求输入WiFi SSID与密码)
- 更新源 — 安装必要软件(vim git htop curl python3)– 开启中文支持(时区+区域)
- (可选)安装全部Kali工具
- (可选)更新全部软件包到最新版本.
----------
附录:
此脚本的内容如下:
#!/bin/bash
function step1() {
clear
echo "Disable overscan..."
mount /dev/mmcblk0p1 /boot
cat > /boot/config.txt << EOF
disable_overscan=1
EOF
echo ""
echo ""
echo "Configurating APT source..."
rm -f /etc/apt/sources.list
cat > /etc/apt/sources.list << EOF
deb http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
deb-src http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
EOF
echo ""
echo ""
echo "Enable WiFi..."
echo "Provide your WiFi's SSID:"
read ssid
echo "Provide your WiFi's Password:"
read pass
cat >> /etc/network/interfaces << EOF
auto wlan0
allow-hotplug wlan0
iface wlan0 inet dhcp
wpa-ssid "${ssid}"
wpa-psk "${pass}"
EOF
clear
echo "Step 1 completed. Plug in your WiFi dungle now and press any key to reboot."
echo "When Rasberry Pi booted, execute this script again and select STEP 2."
echo ""
echo "Press any key to reboot..."
read a
reboot
}
function step2() {
clear
echo "Updating source..."
echo ""
apt update
echo ""
echo ""
echo "Installing vim git htop curl python3..."
apt -y install vim git htop curl python3
echo ""
echo ""
echo "Enable Chinese support..."
apt install ttf-wqy-microhei ttf-wqy-zenhei xfonts-wqy
update-locale LANG=zh_CN.UTF-8
locale-gen --purge zh_CN.UTF-8
echo "Asia/Shanghai" > /etc/timezone
dpkg-reconfigure -f noninteractive tzdata
clear
echo "Step 2 completed. System language will change to Simplified Chinese after reboot."
echo "You can run this script again to goto optional step 3 & 4."
echo ""
echo "Press any key to reboot..."
read a
reboot
}
function step3() {
echo "Installing ALL Kali tools..."
echo ""
apt -y install dnsenum fierce dmitry maltego tcptraceroute theharvester arping fping hping3 nbtscan p0f nmap unicornscan zenmap amap onesixtyone snmpcheck
clear
echo "All done. Enjoy!"
read a
exit
}
function step4() {
clear
echo "Fully upgrading..."
echo ""
apt -y upgrade
clear
echo "All done. Press any key to exit..."
read a
exit
}
clear
echo "###########################################"
echo "# Kali 2.0 Auto-Config for Raspberry Pi 2 #"
echo "# --------------------------------------- #"
echo "# Author: CYRO4S <https://ralf.ren> #"
echo "# Intro: <https://ralf.ren/1234> #"
echo "###########################################"
echo ""
echo ""
echo "Welcome to Kali 2.0 Auto-Config!"
echo "Let's get started, make sure to follow these steps!"
echo ""
echo "1. Disable overscan -- Configure APT source -- Enable WiFi"
echo "2. Update APT source -- Install useful softwares -- Enable Chinese support"
echo "3. (Optional) Install all Kali tools"
echo "4. (Optional) Do a full upgrade for all softwares"
echo ""
echo "Which step are we now at? (1, 2, 3, 4)"
read num
case "$num" in
[1] ) (step1);;
[2] ) (step2);;
[3] ) (step3);;
[4] ) (step4);;
*) echo "Invalid input, now exiting...";;
esac
