A rule based proxy For Mac based on Clash.
Features
HTTP/HTTPS and SOCKS proxy Surge like configuration GeoIP rule support
Install
You can download from release page:
https://github.com/yichengchen/clashX/releases/download/1.5.5/ClashX.dmg
Config
You can use config generator in Status Bar Menu "Config" section. Config support most of surge rules.
Configuration file at $HOME/.config/clash/config.ini
Below is a simple demo configuration file:
[General]
port = 7890
socks-port = 7891
# A RESTful API for clash
external-controller = 127.0.0.1:8080 // do not change this line when you are using clashX
[Proxy]
# name = ss, server, port, cipher, password
# The types of cipher are consistent with go-shadowsocks2
# support AEAD_AES_128_GCM AEAD_AES_192_GCM AEAD_AES_256_GCM AEAD_CHACHA20_POLY1305 AES-128-CTR AES-192-CTR AES-256-CTR AES-128-CFB AES-192-CFB AES-256-CFB CHACHA20-IETF XCHACHA20 RC4-MD5
Proxy1 = ss, server1, port, AEAD_CHACHA20_POLY1305, password
Proxy2 = ss, server2, port, AEAD_CHACHA20_POLY1305, password
[Proxy Group]
# url-test select which proxy will be used by benchmarking speed to a URL.
# name = url-test, [proxys], url, interval(second)
ProxyAuto = url-test, Proxy1, Proxy2, http://www.google.com/generate_204, 300
Proxy = select, Proxy1, Proxy2 ,ProxyAuto // ProxyAuto should be placed before this line
[Rule]
DOMAIN-SUFFIX,google.com,Proxy
DOMAIN-KEYWORD,google,Proxy
DOMAIN-SUFFIX,ad.com,REJECT
GEOIP,CN,DIRECT
FINAL,,Proxy // notice there are two ","
from https://github.com/yichengchen/clashX/tree/master
https://github.com/briteming/clashX/ )
下载地址:https://github.com/yichengchen/clashX/releases
可以删除所有规则,留着最后的cn和final两条。
( clashx很好用。我主要是把它当作一个转换器使用,自动产生一个本地的http proxy:
127.0.0.1:7890 ,这样本地机器不用再利用privoxy/polipo把本地的socks代理服务器127.0.0.1:1080
转换为http proxy.
使用说明:运行clashx后,点击mac顶部的clashx的图标-“配置”- “生成配置文件” - “生成配置” ,
填入ss账号的4个参数,在remarks栏,取个名字,比如bwg.然后点击ok.
这样就会更新$HOME/.config/clash/config.ini文件,然后设置浏览器的http proxy为127.0.0.1:7890 ,
浏览器即可翻墙。)
----------------------------------------------------
mac上的翻墙辅助工具Clash(可以用作ss/ssr在mac上的客户端程序)
wget https://github.com/Dreamacro/clash/releases/download/v0.15.0/clash-darwin-amd64-v0.15.0.gz
mkdir clash-darwin-amd64-v0.15.0
mv clash-darwin-amd64-v0.15.0.gz clash-darwin-amd64-v0.15.0
cd clash-darwin-amd64-v0.15.0
gzip -d clash-darwin-amd64-v0.15.0.gz
此命令会解压该gz压缩包文件,并会覆盖该gz压缩包文件。会解压出可执行文件clash-darwin-amd64-v0.15.0
cd ~/.config/ (如果不存在该.config目录,则创建它)
mkdir clash && cd clash && nano config.yaml
config.yaml的内容如下:
# port of HTTP
port: 7890
# port of SOCKS5
socks-port: 7891
# redir port for Linux and macOS
redir-port: 7892
allow-lan: false
# Rule / Global/ Direct (default is Rule)
mode: Rule
# set log level to stdout (default is info)
# info / warning / error / debug / silent
log-level: info
# A RESTful API for clash
external-controller: 127.0.0.1:9090
# you can put the static web resource (such as clash-dashboard) to a directory, and clash would serve in `${API}/ui`
# input is a relative path to the configuration directory or an absolute path
# external-ui: folder
# Secret for RESTful API (Optional)
# secret: ""
# experimental feature
experimental:
ignore-resolve-fail: true # ignore dns resolve fail, default value is true
# authentication of local SOCKS5/HTTP(S) server
# authentication:
# - "user1:pass1"
# - "user2:pass2"
# dns:
# enable: true # set true to enable dns (default is false)
# ipv6: false # default is false
# listen: 0.0.0.0:53
# enhanced-mode: redir-host # or fake-ip
# # fake-ip-range: 198.18.0.1/16 # if you don't know what it is, don't change it
# nameserver:
# - 114.114.114.114
# - tls://dns.rubyfish.cn:853 # dns over tls
# - https://1.1.1.1/dns-query # dns over https
# fallback: # concurrent request with nameserver, fallback used when GEOIP country isn't CN
# - tcp://1.1.1.1
Proxy:
# shadowsocks
# The types of cipher are consistent with go-shadowsocks2
# support AEAD_AES_128_GCM AEAD_AES_192_GCM AEAD_AES_256_GCM AEAD_CHACHA20_POLY1305 AES-128-CTR AES-192-CTR AES-256-CTR AES-128-CFB AES-192-CFB AES-256-CFB CHACHA20-IETF XCHACHA20
# In addition to what go-shadowsocks2 supports, it also supports chacha20 rc4-md5 xchacha20-ietf-poly1305
- { name: "ss1", type: ss, server: ss-server-ip, port: ss-server-port, cipher: AES-256-CFB, password: the-password, udp: false }
# old obfs configuration remove after prerelease
- name: "ss2"
type: ss
server: server
port: 443
cipher: AEAD_CHACHA20_POLY1305
password: "password"
plugin: obfs
plugin-opts:
mode: tls # or http
# host: bing.com
- name: "ss3"
type: ss
server: server
port: 443
cipher: AEAD_CHACHA20_POLY1305
password: "password"
plugin: v2ray-plugin
plugin-opts:
mode: websocket # no QUIC now
# tls: true # wss
# skip-cert-verify: true
# host: bing.com
# path: "/"
# headers:
# custom: value
Proxy Group:
# url-test select which proxy will be used by benchmarking speed to a URL.
- { name: "auto", type: url-test, proxies: ["ss1", "ss2"], url: "http://www.gstatic.com/generate_204", interval: 300 }
# fallback select an available policy by priority. The availability is tested by accessing an URL, just like an auto url-test group.
- { name: "fallback-auto", type: fallback, proxies: ["ss1", "ss2"], url: "http://www.gstatic.com/generate_204", interval: 300 }
# load-balance: The request of the same eTLD will be dial on the same proxy.
- { name: "load-balance", type: load-balance, proxies: ["ss1", "ss2"], url: "http://www.gstatic.com/generate_204", interval: 300 }
# select is used for selecting proxy or proxy group
# you can use RESTful API to switch proxy, is recommended for use in GUI.
- { name: "Proxy", type: select, proxies: ["ss1", "ss2", "auto"] }
Rule:
- DOMAIN-SUFFIX,google.com,auto
- DOMAIN-SUFFIX,fc2.com,Proxy
- DOMAIN-SUFFIX,epochtimes.com,Proxy
- DOMAIN-SUFFIX,secretchina.com,Proxy
- DOMAIN-SUFFIX,dongtaiwang.com,Proxy
- DOMAIN-SUFFIX,ntdtv.com,Proxy
- DOMAIN-KEYWORD,google,auto
- DOMAIN,google.com,auto
- DOMAIN-SUFFIX,ad.com,REJECT
- IP-CIDR,127.0.0.0/8,DIRECT
# rename SOURCE-IP-CIDR and would remove after prerelease
- SRC-IP-CIDR,192.168.1.201/32,DIRECT
- GEOIP,CN,DIRECT
- DST-PORT,80,DIRECT
- SRC-PORT,7777,DIRECT
# FINAL would remove after prerelease
# you also can use `FINAL,Proxy` or `FINAL,,Proxy` now
- FINAL,,Proxy
cd ~/clash-darwin-amd64-v0.15.0/
./clash-darwin-amd64-v0.15.0 -d ~/.config/clash/
会显示:
INFO[0000] RESTful API listening at: 127.0.0.1:9090
INFO[0000] SOCKS proxy listening at: 127.0.0.1:7891
INFO[0000] HTTP proxy listening at: 127.0.0.1:7890
保持此窗口不要关闭,然后设置浏览器的SOCKS5 proxy为127.0.0.1 ,端口7891 或者
HTTP proxy为127.0.0.1 ,端口7890 ,浏览器即可翻墙。
以后,每次遇到一个被封的网站,就编辑配置文件~/.config/clash/config.yaml, 把该网站的根域名xyz.com以格式:
- DOMAIN-SUFFIX,xyz.com,Proxy 添加在- DOMAIN-SUFFIX,google.com,auto的下一行。然后在~/clash-darwin-amd64-v0.15.0/里面,重新运行:
./clash-darwin-amd64-v0.15.0 -d ~/.config/clash/
项目地址:https://github.com/Dreamacro/clash/
下载地址:https://github.com/Dreamacro/clash/releases
---------------------------------------------
A GUI proxy client for Windows / Mac / Ubuntu Desktop based on Clash and Electron.
Features
- Easy to use interface.
- Build-in Clash binary.
- GUI configuration.
- Remote subscription support.
- Server speed test.
- Set as system proxy (Windows & macOS only).
- Start with system.
Installation
If you meet binary singing issue on Apple & Windows operating system.
Screenshots
 |
 |
|---|---|
 |
 |
Build
- Clone this project & run
yarn install - Run
node pre-build.jsto download clash binary for current platform. - Run
yarn startto start dev server for webpage. - Run
yarn start:electronto start electron main process. Or hit run button inVSCode.
Pack
- Run
yarn run packand wait.
Configuration
-
Where is my configuration files & how can I modify them?To check your configuration files for
Clash&Clashy, click on the folder icon in status panel.Clashconfiguration file folder will opened automatically and navigate to parent folder you will seeClashyconfiguration files namedclashy-configs. -
Can I change clash external controller port & secrets in configuration file?You can but you need to modify
Clashy's source code to make it work.
配置文件
如果提供了订阅链接

如果没有提供订阅链接
在线转换工具
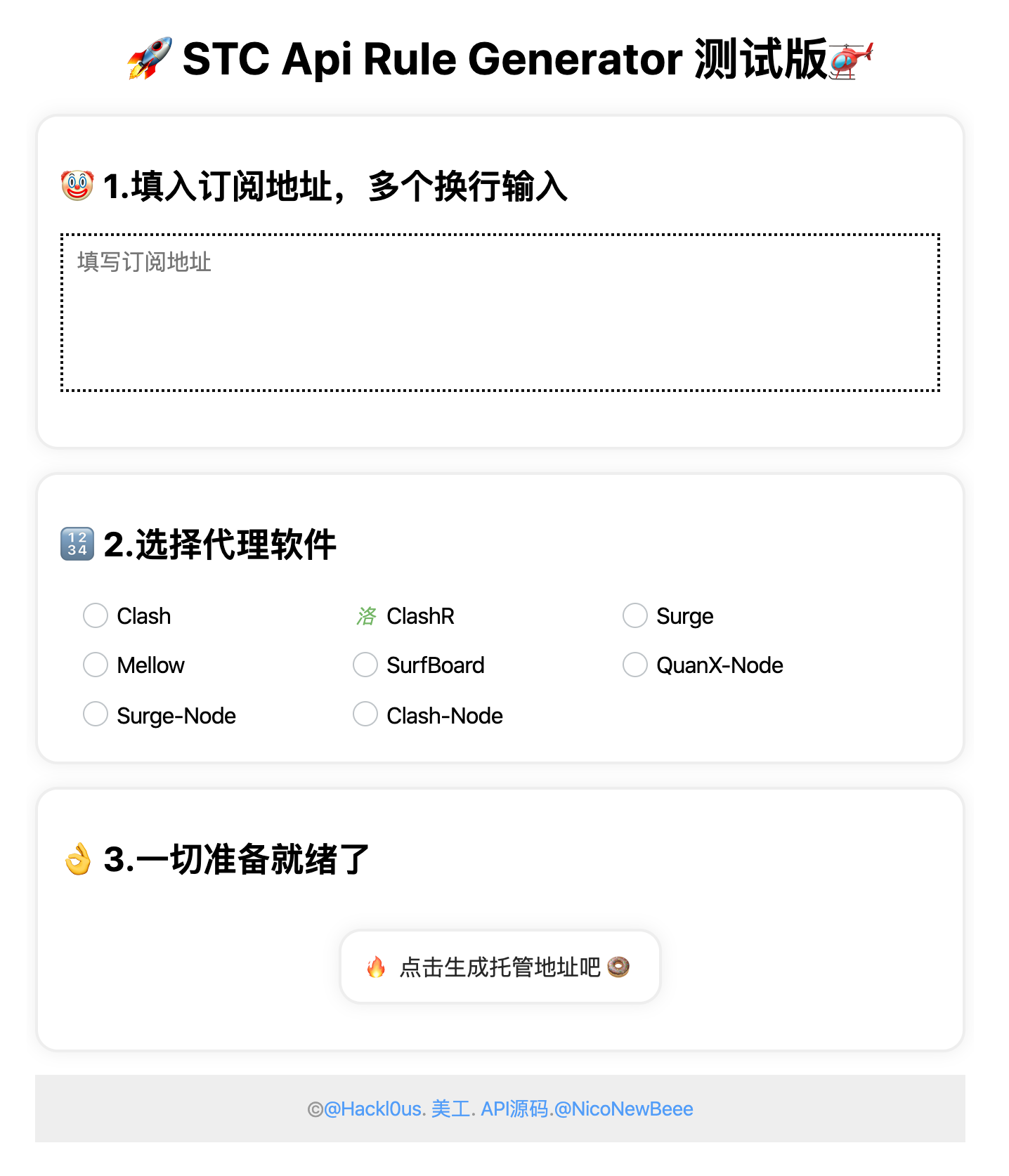
自己写配置文件
# 代理节点这里,我们要修改这里面的内容。这里以某个机场为例,大同小异。1. 登陆云图小镇的用户控制台,左边找到“使用节点”,点进去。
2. 如图我们可以看到有两种节点,第一种标注着“扫码端口xxxx”,这种节点只支持ssr,所以Clash不能用。我们需要的是标注着“扫码使用”的节点,点进去。



name 对应节点名称,可以随便写
type 不要动,保留为预设的ss
server 对应的是“节点地址”
port 对应的是“端口”
cipher 对应的加密方式,这里要用大写,比如云图网页上写的rc4-md5,你要改成RC4-MD5
password 对应的是密码,注意引号不要删
plugin 保留为obfs不要动
mode 对应混淆,云图网页上写的http_post这里只要写http
host 对应混淆参数

它默认是这样的:
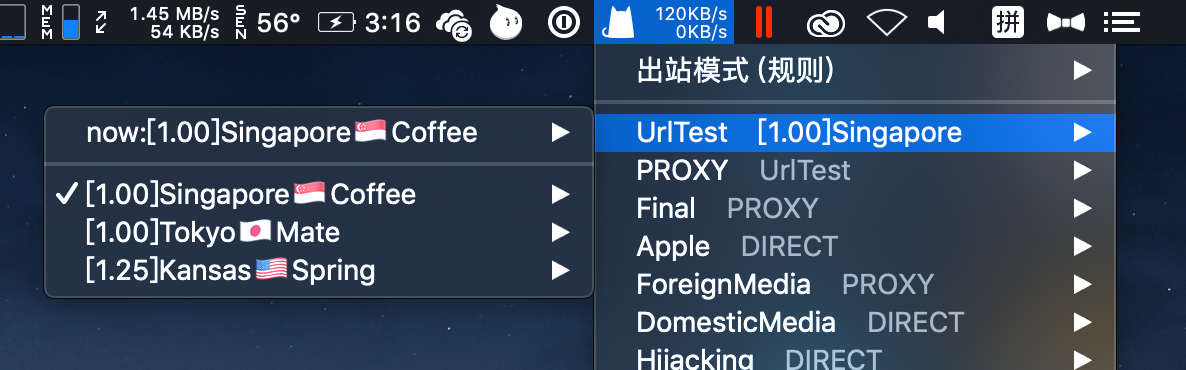
- { name: “UrlTest”, type: url-test, proxies: [“1”, “2”, “3”,”4"], url: “http://www.gstatic.com/generate_204", interval: 300 }
- { name: "UrlTest", type: url-test, proxies: ["[1.25]Kansas🇺🇸Spring", "[1.00]Tokyo🇯🇵Mate", "[1.00]Singapore🇸🇬Coffee"], url: "http://www.gstatic.com/generate_204", interval: 300 }
- { name: “PROXY”, type: select, proxies: [“UrlTest”, “1”, “2”, “3”,”4"] }
- { name: "PROXY", type: select, proxies: ["UrlTest", "[1.25]Kansas🇺🇸Spring", "[1.00]Tokyo🇯🇵Mate", "[1.00]Singapore🇸🇬Coffee" }
至此,配置文件已经修改完毕可以使用了,如果想了解组策略如何使用,请继续往下看:
- DOMAIN,aod.itunes.apple.com,Apple
- DOMAIN,audio.itunes.apple.com,Apple
- DOMAIN,audio-ssl.itunes.apple.com,Apple
- DOMAIN,streamingaudio.itunes.apple.com,Apple
- { name: "Apple", type: select, proxies: ["DIRECT", "PROXY"] }
- { name: "Apple", type: select, proxies: ["DIRECT", "PROXY", "[1.25]Kansas🇺🇸Spring"] }
客户端的使用
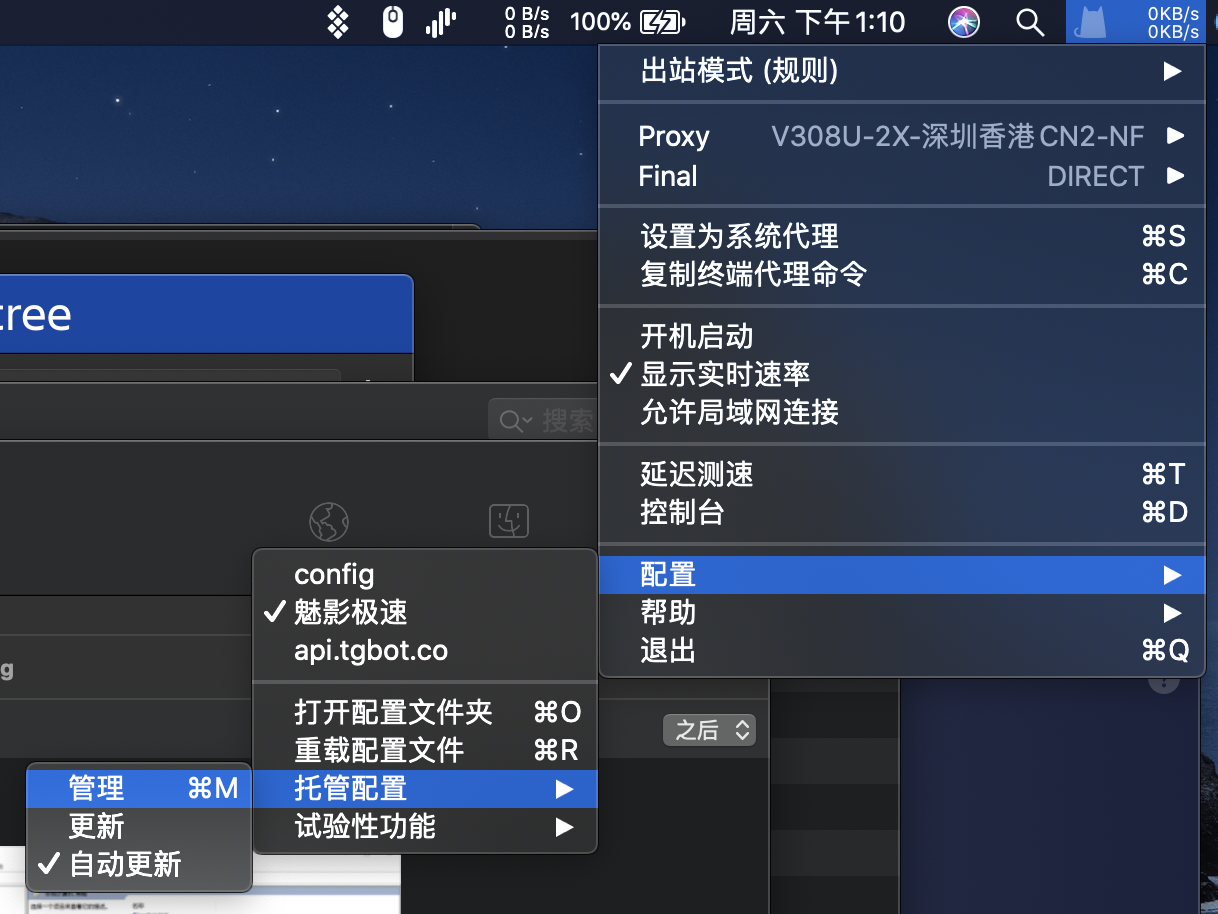
ClashX
1. 打开后要安装一些内容,输入密码后安装






Clash for Android
- 把配置文件弄到手机里。
- 打开 app,点击 Profiles — New Profile — File 选择本地配置文件【如果是获得的托管链接,这里选择 url 并填写托管链接】
- 点击“Stopped”按钮,状态变成 Running,即可使用。


Clash for Windows
- 建议下载 exe 版本安装
- 安装后运行,在状态栏可以找到图标,双击打开 Dashboard




from https://medium.com/@muchenran2/clash-%E5%B8%B8%E7%94%A8%E5%AE%A2%E6%88%B7%E7%AB%AF%E4%BD%BF%E7%94%A8%E6%95%99%E7%A8%8B-%E7%AE%80%E6%98%93%E7%89%88-c77aeb2a10c
A GUI proxy client for Windows / Mac / Ubuntu Desktop based on Clash and Electron. Windows / Mac / Ubuntu 适用的Clash客户端.
Clashy
-
Dialectal, England: wet, showery
Teresa: Hey Danielle look at my diamond encrusted dildo my juice-head husband gave me!!! You Prostitution Whore!!!!Danielle: You're such a Clashy Bitch Teresa... why don't you go flip a table again...
- When two people’s personalities and beliefs clash to the point where one or both really dislike the other. The dislike may or may not be explicitly expressed.
John (super conservative southern male): I think women should have to meet the same physical standards as men in certain jobs, regardless of what biology dictates about that matter.Sheila (politically moderate from North Dakota): Stares judementally with one eye brow raised(A different day) John: Oh hey Sheila! Wanna go out to lunch with me sometime?Sheila: trying to hide her disdain Oh ya,. About that, I have a boyfriend. (She doesn’t).John (in his thoughts): Idk, I guess we’re just really clashy.
from https://github.com/SpongeNobody/Clashy
https://github.com/SpongeNobody/Clashy/releases
--------
https://github.com/whojave/clashr
https://github.com/zengzhengkevin/clashr
------------------------------------
ShadowClash is a rewritten version of ClashX by Qt5.
ShadowClash
Features
- Cross platform Support
- HTTP/HTTPS and SOCKS protocol
- Surge like configuration
- GeoIP rule support
- Support Vmess/Shadowsocks/Socks5
- Support for Netfilter TCP redirect
- EnhanceMode support(tun2socks)
- ClashR support
Install
Build
- Clone the Repo
git clone https://github.com/TheWanderingCoel/ShadowClash.git - Download and build deps
python3 install_dependency.py - Build clash core.
cd clash python3 build_clash.py cd .. - Or build the clashR core.
cd clashr python3 build_clashr.py cd .. - Run qmake
mkdir build && cd build qmake ../ - Run make
make -j8
Config
$HOME/.config/clashconfig.ymal. You can use your custom config name and switch config in menu Config section.config.ymal file. The General section settings in your custom config file would be ignored.Translate
Sponsor
Special Thanks
-
clash Under GPL-3.0 license
-
clashR Under GPL-3.0 license
-
yaml-cpp Under MIT license
-
plog Under MPL-2.0 license
-
clashX Under GPL-3.0 license
-
openVPN(Tap Driver) Under MIT and GPLv2 license
-
go-tun2socks Under MIT license
-
ieproxy Under BSL-1.0 license
Other Softwares
Your star is my energy to develop more good softwares.
-
BiliBiliHelper Under GPL-3.0 license
-
PixivDownloader Under GPL-3.0 license
目标
- 配置 Clash 使其走 vmess 协议来处理透明代理流量。
- 配置 iptables 转发流量
注意:本文是基于安装了 Debian 系统的的软路由配置的,Openwrt 也可以参考自行修改。
Clash优势
相比原生的 V2Ray,Clash 的优势如下:
- 灵活管理 proxy,支持不同的策略来选择最优的 proxy
- 内置 DNS,支持 DOH
- 基于规则来的流量转发
Clash的安装配置
安装
TARGET=/usr/local/clash
[ -e $TARGET ] || mkdir $TARGET
VERSION=v1.0.0
FILENAME=clash-linux-amd64-$VERSION
curl -sLO https://github.com/Dreamacro/clash/releases/download/$VERSION/$FILENAME.gz
gunzip $FILENAME.gz
mv $FILENAME $TARGET/clash
chmod 755 $TARGET/clashClash的配置
配置这里我是基于这个模板修改的,精简了一些配置。
配置放在 /usr/local/clash/config.yml
port: 7890
socks-port: 7891
redir-port: 7892
allow-lan: true
mode: Rule
log-level: info
external-controller: 127.0.0.1:9090
# secret: ""
dns:
enable: true
listen: 0.0.0.0:853
enhanced-mode: redir-host
nameserver:
- 'tls://dns.rubyfish.cn:853'
- '114.114.114.114'
fallback:
- 'tls://1.1.1.1:853'
- 'tls://dns.google'
proxies:
# 这两个tlb proxy配合我的tlb项目使用的,因为clash内置了proxy选择的策略,所以目前暂时也没有开发的动力
# https://github.com/xdays/tlb
- name: ss-tlb
type: ss
server: 127.0.0.1
port: 443
cipher: rc4-md5
password: changeme
- name: vmess-tlb
type: vmess
server: 127.0.0.1
port: 345
uuid: changeme
alterId: 64
cipher: aes-128-gcm
network: ws
ws-path: /
ws-headers:
Host: foo.xdays.me
tls: true
- name: vmess-hkg01
type: vmess
server: 1.1.1.1
port: 443
uuid: changeme
alterId: 64
cipher: aes-128-gcm
network: ws
ws-path: /
ws-headers:
Host: foo.xdays.me
tls: true
- name: vmess-hkg02
type: vmess
server: 1.1.1.2
port: 443
uuid: changeme
alterId: 64
cipher: aes-128-gcm
network: ws
ws-path: /
ws-headers:
Host: foo.xdays.me
tls: true
# 代理组策略
proxy-groups:
# url-test 通过指定的 URL 测试并选择延迟最低的节点
- name: "UrlTest"
type: url-test
proxies:
- "vmess-hkg01"
- "vmess-hkg02"
url: 'http://www.gstatic.com/generate_204'
interval: 300
# fallback 通过指定的 URL 测试并选择可用的节点,当 1 故障不可用时自动切换到 2 以此类推
- name: "Fallback"
type: fallback
proxies:
- "vmess-hkg01"
url: 'http://www.gstatic.com/generate_204'
interval: 300
# 代理节点选择
- name: "PROXY"
type: select
proxies:
- "UrlTest"
- "vmess-tlb"
- "vmess-hkg01"
# 白名单模式 PROXY,黑名单模式 DIRECT
- name: "Final"
type: select
proxies:
- "PROXY"
- "DIRECT"
# 运营商及声名狼藉网站劫持
- name: "Hijacking"
type: select
proxies:
- "REJECT"
- "DIRECT"
# 规则
rules:
# Internet Service Providers Hijacking 运营商劫持
- DOMAIN-SUFFIX,17gouwuba.com,Hijacking
- DOMAIN-SUFFIX,186078.com,Hijacking
- DOMAIN-SUFFIX,189zj.cn,Hijacking
- DOMAIN-SUFFIX,285680.com,Hijacking
- DOMAIN-SUFFIX,3721zh.com,Hijacking
- DOMAIN-SUFFIX,4336wang.cn,Hijacking
- DOMAIN-SUFFIX,51chumoping.com,Hijacking
- DOMAIN-SUFFIX,51mld.cn,Hijacking
- DOMAIN-SUFFIX,51mypc.cn,Hijacking
- DOMAIN-SUFFIX,58mingri.cn,Hijacking
- DOMAIN-SUFFIX,58mingtian.cn,Hijacking
- DOMAIN-SUFFIX,5vl58stm.com,Hijacking
- DOMAIN-SUFFIX,6d63d3.com,Hijacking
- DOMAIN-SUFFIX,7gg.cc,Hijacking
- DOMAIN-SUFFIX,91veg.com,Hijacking
- DOMAIN-SUFFIX,9s6q.cn,Hijacking
- DOMAIN-SUFFIX,adsame.com,Hijacking
- DOMAIN-SUFFIX,aiclk.com,Hijacking
- DOMAIN-SUFFIX,akuai.top,Hijacking
- DOMAIN-SUFFIX,atplay.cn,Hijacking
- DOMAIN-SUFFIX,baiwanchuangyi.com,Hijacking
- DOMAIN-SUFFIX,beerto.cn,Hijacking
- DOMAIN-SUFFIX,beilamusi.com,Hijacking
- DOMAIN-SUFFIX,benshiw.net,Hijacking
- DOMAIN-SUFFIX,bianxianmao.com,Hijacking
- DOMAIN-SUFFIX,bryonypie.com,Hijacking
- DOMAIN-SUFFIX,cishantao.com,Hijacking
- DOMAIN-SUFFIX,cszlks.com,Hijacking
- DOMAIN-SUFFIX,cudaojia.com,Hijacking
- DOMAIN-SUFFIX,dafapromo.com,Hijacking
- DOMAIN-SUFFIX,daitdai.com,Hijacking
- DOMAIN-SUFFIX,dsaeerf.com,Hijacking
- DOMAIN-SUFFIX,dugesheying.com,Hijacking
- DOMAIN-SUFFIX,dv8c1t.cn,Hijacking
- DOMAIN-SUFFIX,echatu.com,Hijacking
- DOMAIN-SUFFIX,erdoscs.com,Hijacking
- DOMAIN-SUFFIX,fan-yong.com,Hijacking
- DOMAIN-SUFFIX,feih.com.cn,Hijacking
- DOMAIN-SUFFIX,fjlqqc.com,Hijacking
- DOMAIN-SUFFIX,fkku194.com,Hijacking
- DOMAIN-SUFFIX,freedrive.cn,Hijacking
- DOMAIN-SUFFIX,gclick.cn,Hijacking
- DOMAIN-SUFFIX,goufanli100.com,Hijacking
- DOMAIN-SUFFIX,goupaoerdai.com,Hijacking
- DOMAIN-SUFFIX,gouwubang.com,Hijacking
- DOMAIN-SUFFIX,gzxnlk.com,Hijacking
- DOMAIN-SUFFIX,haoshengtoys.com,Hijacking
- DOMAIN-SUFFIX,hyunke.com,Hijacking
- DOMAIN-SUFFIX,ichaosheng.com,Hijacking
- DOMAIN-SUFFIX,ishop789.com,Hijacking
- DOMAIN-SUFFIX,jdkic.com,Hijacking
- DOMAIN-SUFFIX,jiubuhua.com,Hijacking
- DOMAIN-SUFFIX,jsncke.com,Hijacking
- DOMAIN-SUFFIX,junkucm.com,Hijacking
- DOMAIN-SUFFIX,jwg365.cn,Hijacking
- DOMAIN-SUFFIX,kawo77.com,Hijacking
- DOMAIN-SUFFIX,kualianyingxiao.cn,Hijacking
- DOMAIN-SUFFIX,kumihua.com,Hijacking
- DOMAIN-SUFFIX,ltheanine.cn,Hijacking
- DOMAIN-SUFFIX,maipinshangmao.com,Hijacking
- DOMAIN-SUFFIX,minisplat.cn,Hijacking
- DOMAIN-SUFFIX,mkitgfs.com,Hijacking
- DOMAIN-SUFFIX,mlnbike.com,Hijacking
- DOMAIN-SUFFIX,mobjump.com,Hijacking
- DOMAIN-SUFFIX,nbkbgd.cn,Hijacking
- DOMAIN-SUFFIX,newapi.com,Hijacking
- DOMAIN-SUFFIX,pinzhitmall.com,Hijacking
- DOMAIN-SUFFIX,poppyta.com,Hijacking
- DOMAIN-SUFFIX,qianchuanghr.com,Hijacking
- DOMAIN-SUFFIX,qichexin.com,Hijacking
- DOMAIN-SUFFIX,qinchugudao.com,Hijacking
- DOMAIN-SUFFIX,quanliyouxi.cn,Hijacking
- DOMAIN-SUFFIX,qutaobi.com,Hijacking
- DOMAIN-SUFFIX,ry51w.cn,Hijacking
- DOMAIN-SUFFIX,sg536.cn,Hijacking
- DOMAIN-SUFFIX,sifubo.cn,Hijacking
- DOMAIN-SUFFIX,sifuce.cn,Hijacking
- DOMAIN-SUFFIX,sifuda.cn,Hijacking
- DOMAIN-SUFFIX,sifufu.cn,Hijacking
- DOMAIN-SUFFIX,sifuge.cn,Hijacking
- DOMAIN-SUFFIX,sifugu.cn,Hijacking
- DOMAIN-SUFFIX,sifuhe.cn,Hijacking
- DOMAIN-SUFFIX,sifuhu.cn,Hijacking
- DOMAIN-SUFFIX,sifuji.cn,Hijacking
- DOMAIN-SUFFIX,sifuka.cn,Hijacking
- DOMAIN-SUFFIX,smgru.net,Hijacking
- DOMAIN-SUFFIX,taoggou.com,Hijacking
- DOMAIN-SUFFIX,tcxshop.com,Hijacking
- DOMAIN-SUFFIX,tjqonline.cn,Hijacking
- DOMAIN-SUFFIX,topitme.com,Hijacking
- DOMAIN-SUFFIX,tt3sm4.cn,Hijacking
- DOMAIN-SUFFIX,tuia.cn,Hijacking
- DOMAIN-SUFFIX,tuipenguin.com,Hijacking
- DOMAIN-SUFFIX,tuitiger.com,Hijacking
- DOMAIN-SUFFIX,websd8.com,Hijacking
- DOMAIN-SUFFIX,wsgblw.com,Hijacking
- DOMAIN-SUFFIX,wx16999.com,Hijacking
- DOMAIN-SUFFIX,xchmai.com,Hijacking
- DOMAIN-SUFFIX,xiaohuau.xyz,Hijacking
- DOMAIN-SUFFIX,ygyzx.cn,Hijacking
- DOMAIN-SUFFIX,yinmong.com,Hijacking
- DOMAIN-SUFFIX,yitaopt.com,Hijacking
- DOMAIN-SUFFIX,yjqiqi.com,Hijacking
- DOMAIN-SUFFIX,yukhj.com,Hijacking
- DOMAIN-SUFFIX,zhaozecheng.cn,Hijacking
- DOMAIN-SUFFIX,zhenxinet.com,Hijacking
- DOMAIN-SUFFIX,zlne800.com,Hijacking
- DOMAIN-SUFFIX,zunmi.cn,Hijacking
- DOMAIN-SUFFIX,zzd6.com,Hijacking
- IP-CIDR,39.107.15.115/32,Hijacking,no-resolve
- IP-CIDR,47.89.59.182/32,Hijacking,no-resolve
- IP-CIDR,103.49.209.27/32,Hijacking,no-resolve
- IP-CIDR,123.56.152.96/32,Hijacking,no-resolve
# > ChinaTelecom
- IP-CIDR,61.160.200.223/32,Hijacking,no-resolve
- IP-CIDR,61.160.200.242/32,Hijacking,no-resolve
- IP-CIDR,61.160.200.252/32,Hijacking,no-resolve
- IP-CIDR,61.174.50.214/32,Hijacking,no-resolve
- IP-CIDR,111.175.220.163/32,Hijacking,no-resolve
- IP-CIDR,111.175.220.164/32,Hijacking,no-resolve
- IP-CIDR,122.229.8.47/32,Hijacking,no-resolve
- IP-CIDR,122.229.29.89/32,Hijacking,no-resolve
- IP-CIDR,124.232.160.178/32,Hijacking,no-resolve
- IP-CIDR,175.6.223.15/32,Hijacking,no-resolve
- IP-CIDR,183.59.53.237/32,Hijacking,no-resolve
- IP-CIDR,218.93.127.37/32,Hijacking,no-resolve
- IP-CIDR,221.228.17.152/32,Hijacking,no-resolve
- IP-CIDR,221.231.6.79/32,Hijacking,no-resolve
- IP-CIDR,222.186.61.91/32,Hijacking,no-resolve
- IP-CIDR,222.186.61.95/32,Hijacking,no-resolve
- IP-CIDR,222.186.61.96/32,Hijacking,no-resolve
- IP-CIDR,222.186.61.97/32,Hijacking,no-resolve
# > ChinaUnicom
- IP-CIDR,106.75.231.48/32,Hijacking,no-resolve
- IP-CIDR,119.4.249.166/32,Hijacking,no-resolve
- IP-CIDR,220.196.52.141/32,Hijacking,no-resolve
- IP-CIDR,221.6.4.148/32,Hijacking,no-resolve
# > ChinaMobile
- IP-CIDR,114.247.28.96/32,Hijacking,no-resolve
- IP-CIDR,221.179.131.72/32,Hijacking,no-resolve
- IP-CIDR,221.179.140.145/32,Hijacking,no-resolve
# > Dr.Peng
# - IP-CIDR,10.72.25.0/24,Hijacking,no-resolve
- IP-CIDR,115.182.16.79/32,Hijacking,no-resolve
- IP-CIDR,118.144.88.126/32,Hijacking,no-resolve
- IP-CIDR,118.144.88.215/32,Hijacking,no-resolve
- IP-CIDR,118.144.88.216/32,Hijacking,no-resolve
- IP-CIDR,120.76.189.132/32,Hijacking,no-resolve
- IP-CIDR,124.14.21.147/32,Hijacking,no-resolve
- IP-CIDR,124.14.21.151/32,Hijacking,no-resolve
- IP-CIDR,180.166.52.24/32,Hijacking,no-resolve
- IP-CIDR,211.161.101.106/32,Hijacking,no-resolve
- IP-CIDR,220.115.251.25/32,Hijacking,no-resolve
- IP-CIDR,222.73.156.235/32,Hijacking,no-resolve
# Local Area Network
- IP-CIDR,192.168.0.0/16,DIRECT
- IP-CIDR,10.0.0.0/8,DIRECT
- IP-CIDR,172.16.0.0/12,DIRECT
- IP-CIDR,127.0.0.0/8,DIRECT
- IP-CIDR,100.64.0.0/10,DIRECT
# GeoIP China
- GEOIP,CN,DIRECT
- MATCH,Final透明代理配置
Clash 的透明代理需要做两步:
- DNS 解析要经过 Clash 自己监听的 DNS 服务, 我这里是 UDP 的 853 端口
- iptables 把流量 redirect 给 clash
先说第一步,我的做法是用 dnsmasq 来作为局域网的 dhcp 和 dns server,然后 dnsmasq 将 dns 请求转发给 clash 的 853 端口,dnsmasq 的配置如下:
bogus-priv
no-resolv
server=127.0.0.1#853
domain=lan,192.168.2.0/24
dhcp-range=192.168.2.100,192.168.2.200,12h
dhcp-leasefile=/var/lib/misc/dnsmasq.leases
cache-size=150再说第二步,iptables 的配置也很简单,我写了一个脚本来开关 iptables 规则
脚本放在 /usr/local/clash/proxy.sh
#!/bin/bash
DNSCONF=/etc/dnsmasq.d/local
echo 1 > /proc/sys/net/ipv4/ip_forward
start() {
# TCP Redirect
# Create new chain
echo "create a new chain"
iptables -t nat -N CLASH
# Ignore LANs and any other addresses you'd like to bypass the proxy
# See Wikipedia and RFC5735 for full list of reserved networks.
iptables -t nat -A CLASH -d 0.0.0.0/8 -j RETURN
iptables -t nat -A CLASH -d 10.0.0.0/8 -j RETURN
iptables -t nat -A CLASH -d 127.0.0.0/8 -j RETURN
iptables -t nat -A CLASH -d 169.254.0.0/16 -j RETURN
iptables -t nat -A CLASH -d 172.16.0.0/12 -j RETURN
iptables -t nat -A CLASH -d 192.168.0.0/16 -j RETURN
iptables -t nat -A CLASH -d 224.0.0.0/4 -j RETURN
iptables -t nat -A CLASH -d 240.0.0.0/4 -j RETURN
iptables -t nat -A CLASH -s 192.168.2.0/24 -p tcp -j REDIRECT --to-ports 7892
# apply redirect for traffic forworded by this proxy
echo "apply the clash chain"
iptables -t nat -A PREROUTING -p tcp -j CLASH
# apply redirect for proxy itself
# for i in $OID; do
# iptables -t nat -A OUTPUT -m owner --uid-owner $i -j RETURN
# done
# iptables -t nat -A OUTPUT -p tcp -j CLASH
echo "change dns server"
use-gfw-dns
}
stop() {
iptables -t nat -D PREROUTING -p tcp -j CLASH
iptables -t nat -F CLASH
iptables -t nat -X CLASH
use-normal-dns
}
status() {
echo "==== Iptable rules ===="
iptables -t nat -nL
echo
echo "==== DNS Sever===="
grep "^server=" $DNSCONF
}
use-normal-dns() {
# 这里要改成一个你自己的dns服务器
sed -i '/server=.*/s/.*/server=192.168.1.1/' $DNSCONF
systemctl restart dnsmasq
}
use-gfw-dns() {
sed -i '/server=.*/s/.*/server=127.0.0.1#853/' $DNSCONF
systemctl restart dnsmasq
}
case $1 in
start)
start
;;
stop)
stop
;;
status)
status
;;
*)
echo "$0 start | stop | status"
;;
esac改下可执行权限
chmod 755 /usr/local/clash/proxy.sh这个脚本里还包括的切换 dnsmasq 的 dns 配置的操作,因为如果 clash 停了整个局域网所有机器的 dns 解析就会失败,这是配合后边一键启停翻墙做准备的。
一键开关透明代理
编辑 /etc/systemd/system/clash.service
[Unit]
Description=Clash Service
After=network.target
Wants=network.target
[Service]
# User=nobody
# Group=nobody
Type=simple
PIDFile=/run/clash.pid
ExecStartPre=/usr/local/clash/proxy.sh start
ExecStart=/usr/local/clash/clash -d /usr/local/clash/
ExecStopPost=/usr/local/clash/proxy.sh stop
Restart=on-failure
RestartPreventExitStatus=23
[Install]
WantedBy=multi-user.target然后加载配置,开机启动透明代理
systemctl daemon-reload
systemctl start clash
systemctl enable clashSetting up Clash as Second Gateway for LAN
Less painful way setting up a second gateway using Clash, IPset and iptables.
Prerequisite
- https://github.com/comzyh/clash, (https://github.com/comzyh/clash/tree/add-water分支更好)
- Open sourced tun support
- Debian 10
- Proxy provider
- Shadowsocks or whatever supported by clash, Dler Cloud for example
Steps
1 Setup Tun
TUN_NAME=clash0
sudo ip tuntap add mode tun user clash name $TUN_NAME
sudo ip link set $TUN_NAME up
# or sudo ifconfig utun up
2 Setup iptables
iptables -t mangle -N CLASH # Create Clash Chain
iptables -t mangle -A CLASH -d 0.0.0.0/8 -j RETURN
iptables -t mangle -A CLASH -d 10.0.0.0/8 -j RETURN
iptables -t mangle -A CLASH -d 127.0.0.0/8 -j RETURN
iptables -t mangle -A CLASH -d 169.254.0.0/16 -j RETURN
iptables -t mangle -A CLASH -d 172.16.0.0/12 -j RETURN
iptables -t mangle -A CLASH -d 192.168.0.0/16 -j RETURN
iptables -t mangle -A CLASH -d 224.0.0.0/4 -j RETURN
iptables -t mangle -A CLASH -d 240.0.0.0/4 -j RETURN
# ipset can be enabled optionally.
# iptables -t mangle -A CLASH -m set --match-set CN dst -j RETURN
iptables -t mangle -A CLASH -j MARK --set-xmark 129
iptables -t mangle -A PREROUTING -j CLASH # have traffic come to the CLASH chain
# if you need to have the local machine(the machine clash is running on) traffic to go through clash TUN
# note: you should have clash running under the user `clash', see below systemd script
# iptables -t mangle -A OUTPUT -m owner --uid-owner clash -j RETURN
# iptables -t mangle -A OUTPUT -j CLASH
3 Setup route
ip route add default dev $ table 129
ip rule add fwmark 129 $TUN_NAME lookup 129
4 Checkpoint 1
At this stage, all the traffic routed by this machine will be tagged with fwmark 129 and redirected to $TUN_NAME.
Feel free to change the number 129 to whatever you like.
5 Setup clash
To have clash handle the traffic on $TUN_NAME, we need to setup clash properly.
5.1 Install
Download the binary from https://github.com/comzyh/clash/releases and put it under /usr/bin/clash. For example:
curl -sL https://github.com/comzyh/clash/releases/download/20210310/clash-linux-amd64 -o /usr/bin/clash
5.2 systemd script
Note The user should match that one speficied in the iptable rules above.
cat /lib/systemd/system/clash@.service
[Unit]
Description=Clash
After=network.target
[Service]
Type=simple
User=%i
Restart=always
ExecStart=/usr/bin/clash -d /home/wtf/clash
AmbientCapabilities=CAP_NET_BIND_SERVICE CAP_NET_ADMIN
CapabilityBoundingSet=CAP_NET_BIND_SERVICE CAP_NET_ADMIN
[Install]
WantedBy=multi-user.target
systemctl enable clash@clash
5.3 clash config
Add this section to your existing config.yaml
Note
The device url should be dev://$TUN_NAME
tun:
enable: true
stack: system
device-url: dev://clash0
# dns-hijack:
# - 10.0.0.5
5.4 Start clash
systemctl enable clash@clash
6 Checkpoint 2
At this stage, you should be able to use this machine as the gateway for you LAN devices.
Note
Don't forget to enable ipv4_forwarding on your machine. In case you need help: https://linuxconfig.org/how-to-turn-on-off-ip-forwarding-in-linux
7 Misc
7.1 Setup ipset
Sometimes you don't really want to route all traffic to the gateway, and that can be done by setting up ipset. By doing this, you can either to have the iptables RETURN all the traffic that is matching a particular ipset or only mark the traffic when it matches.
In my case, I want to have all the China Mainland traffic to be going though the clash tun, so I'll have the script below to update the ipset everyday.
cat /etc/cron.daily/update-ipset.sh
IPSET_BIN=/usr/sbin/ipset
$IPSET_BIN -L CN-new > /dev/null 2>&1
if [ $? -eq 0 ]; then
$IPSET_BIN destroy CN-new
fi
$IPSET_BIN create CN-new hash:net
curl -sL http://www.ipdeny.com/ipblocks/data/countries/cn.zone | xargs -n1 $IPSET_BIN -A CN-new
$IPSET_BIN -L CN > /dev/null 2>&1
if [ $? -ne 0 ]; then
$IPSET_BIN create CN hash:net
fi
$IPSET_BIN swap CN-new CN
$IPSET_BIN destroy CN-new
And have my mangle table:
iptables -t mangle -L
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
RETURN udp -- anywhere anywhere udp dpts:4096:65535
RETURN tcp -- anywhere anywhere tcp dpts:8192:65535
CLASH all -- anywhere anywhere
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
Chain CLASH (1 references)
target prot opt source destination
MARK all -- anywhere anywhere match-set CN dst MARK set 0xc0
7.2 Persistence
-
iptables/ipset
You'll want to use
iptables-persistent/ipset-persistentto have iptables/ipset persistence -
route and tun dev
Use Debian network configuration, an example:
cat /etc/network/interfaces | grep -A 20 clash0 auto clash0 iface clash0 inet manual pre-up ip tuntap add mode tun user clash name $IFACE up ip link set dev $IFACE up post-up ip route add default dev $IFACE table 192 post-up ip rule add fwmark 192 lookup 192 down ip link set dev $IFACE down post-down ip link del dev $IFACE post-down ip route del default dev $IFACE table 192 post-down ip rule del fwmark 192 lookup 192
Summary
You should now be ready to setup the IP of the above machine to be the default gateway on you DHCP service.
Best practive is having a static IP for the above machine and always have a backup gateway in case something went wrong with the second gateway.
All the script sample above are for my personal note and demo purpose only - make sure you understand it and feel free to make any change accordingly.
from https://ibigbug.online/best-practice-for-setting-up-clash-as-second-gateway
---------
Clash的基本配置
规则解释
- DOMAIN-SUFFIX:域名后缀匹配
- DOMAIN:域名匹配
- DOMAIN-KEYWORD:域名关键字匹配
- IP-CIDR:IP段匹配
- SRC-IP-CIDR:源IP段匹配
- GEOIP:GEOIP数据库(国家代码)匹配
- DST-PORT:目标端口匹配
- SRC-PORT:源端口匹配
- MATCH:全匹配(一般放在最后)
基本配置
额外支持特定的字段:
- cfw-latency-timeout:延迟测试超时时间(毫秒),默认3000
- cfw-latency-url:延迟测试URL,默认http://www.gstatic.com/generate_204
- cfw-bypass:系统代理绕过域名或地址,参考 绕过系统代理
- cfw-conn-break-strategy: 切换节点后或切换配置文件后打断连接
- cfw-profiles-path: 自定义 profiles 目录路径 (beta)
这些配置关乎Clash核心是否能正常启动,如非必要,请勿更改
完全配置记录
绕过系统代理
Clash for Windows在v 0.4.5 版本后可以自定义系统代理需要绕过的域名或IP
部分应用检测到系统代理会拒绝响应(例如网易云音乐uwp),此功能用于解决此类问题
设置方式
config.yaml
cfw-bypass类型为数组,item为需要绕过的域名或节点,支持通配符*
最后一行对应系统中“请勿将代理服务器用于本地(Intranet)地址”选项,请确保此项在最底部.
---------------------
An easy-to-use GUI for clash .
EasyClash
A configuration manager app about clash.
Support:
Macos Intel,Macos M1,Donwload EasyClashWinPreview
Add ProxyProvider
QA
sudo xattr -r -d com.apple.quarantine /Applications/EasyClash.app# 1 sudo spctl --master-disable # 2 系统偏好设置 > 安全性与隐私 > 任何来源.
fromhttps://github.com/lwd-temp/EasyClash
--------------------------------------------------------------------------------------------
A Clash GUI based on tauri. Supports Windows, macOS and Linux.
Clash Verge
A Clash GUI based on tauri.
Features
- Full
clashconfig supported, Partialclash premiumconfig supported.- Profiles management and enhancement (by yaml and Javascript). Doc
- Simple UI and supports custom theme color.
- Built-in support Clash.Meta core.
- System proxy setting and guard.
Promotion
- High-performance overseas VPN, free trial, discounted packages, unlock streaming media, the world's first to support Hysteria protocol.
- 高性能海外机场,免费试用,优惠套餐,解锁流媒体,全球首家支持 Hysteria 协议。
- 使用 Clash Verge 专属邀请链接注册送 15 天,每天 1G 流量免费试用:https://panel.dg1.top/#/register?code=sFCDayZf
Install
Download from release. Supports Windows x64, Linux x86_64 and macOS 11+
Or you can build it yourself. Supports Windows, Linux and macOS 10.15+
Notes: If you could not start the app on Windows, please check that you have Webview2 installed.
FAQ
1. macOS "Clash Verge" is damaged and can't be opened
open the terminal and run
sudo xattr -r -d com.apple.quarantine /Applications/Clash\ Verge.appDevelopment
You should install Rust and Nodejs, see here for more details. Then install Nodejs packages.
yarn installThen download the clash binary... Or you can download it from clash premium release and rename it according to tauri config.
# force update to latest version # yarn run check --force yarn run checkThen run
yarn dev # run it in another way if app instance exists yarn dev:diffOr you can build it
yarn build
from


























